Consumer Analytics Market and Today’s Privacy Landscape
Consumer data is extremely valuable in today’s market. According to a study by Grand View Research, the global customer analytics market size reached an impressive estimate of nearly 15 billion dollars in 2023. This sector is poised for significant growth, with experts projecting an annual expansion rate of 19.2% from 2024 to 2030. If these projections hold true, the market is expected to reach a staggering value of approximately 48 billion dollars by 2030.
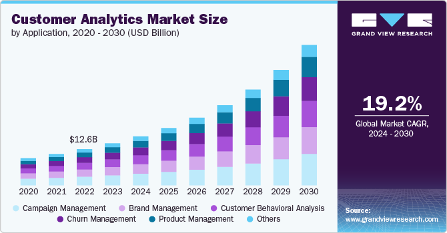
As the value and importance of consumer data continue to grow, so does the need for robust data protection measures and regulations. This shift in focus has led to significant changes in the regulatory landscape, particularly in the United States.
The United States has historically taken a light approach to regulating personal data privacy, focusing mainly on federal laws for specific industries or types of data. However, since 2019, there has been a significant shift, with 19 states enacting comprehensive privacy laws. There is a strong trend and demand for a federal comprehensive data privacy law, driven by the FTC and consumer groups, but such a law has not yet been enacted. Moreover, as companies increasingly conduct business internationally, data processing borders are becoming more fluid, potentially exposing businesses to stricter foreign data privacy regimes like the GDPR with its cross-border data flow requirements.
A “Carrot-and-Stick” Approach to Privacy
Although privacy compliance absolutely requires an investment, there is a strong business case for it, involving a proverbial “carrot and a stick.”
On the one hand, privacy enforcement is on the rise, with the most notable actions including Facebook, now Meta, faced with a staggering $5 billion fine from the FTC in 2019 for violating user privacy and engaging in deceptive practices related to the Cambridge Analytica scandal. More recently, Meta was hit with another €1.2 billion fine for EU-US data transfers that violated GDPR regulations. Similarly, Equifax had to settle for $700 million with the FTC in 2019 due to a massive data breach that exposed the personal information of 147 million people. Unfortunately, fines for privacy violations are common in the telecommunications industry, as well.
![]()
Source: International Association of Privacy Professionals, US State Privacy Legislation Tracker
On the other hand, privacy compliance has been shown to increase customer trust and retention. According to Cisco 2024 Data Privacy Benchmark Study, 95% of respondents reported that the benefits of privacy outweigh its costs. The study showed that the average return on privacy investment was an impressive 160%, and 30% of organizations are experiencing returns of at least twice their privacy investment, highlighting the significant financial advantages of prioritizing privacy compliance.
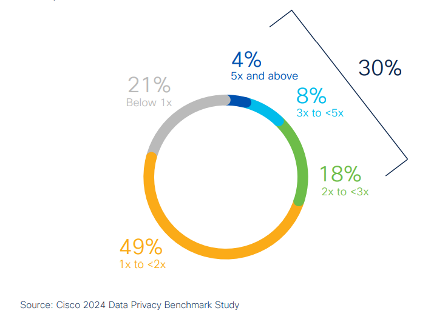
Estimated ROI ranges for respondents, 2023.
Source: Cisco 2024 Data Privacy Benchmark Study
With conventional technology, privacy compliance may be bulky and inefficient. But it doesn’t have to be.
Enter vCon
VCon (short for “virtualized conversations”) is a new open-source protocol developed by Daniel Petrie and Thomas McCarthy-Howe, a digital “container” for data relating to human conversations. VCon streamlines the collection, storage, analysis, and sharing of conversational data and can contain the call recording and/or its contents, metadata (for example, the parties, time, location, and consent information), and attachments (for example, call analytics). Using vCon can empower enterprises to manage their communications more efficiently (espectially, in contact center environments). On top of that, vCon also offers a robust infrastructure for navigating the communications information necessary for privacy law compliance. For example, the ability to search conversations by party enables quick retrieval of consumer data when addressing privacy rights requests.
Privacy Law – In General
Privacy in general can be understood as “the right to be let alone.” It may be helpful to think of it in four aspects:
- personal information (or data) privacy,
- bodily privacy,
- territorial privacy, and
- communications privacy.
In the context of vCon, we will concentrate on data privacy and communications privacy.
Data Privacy
Data privacy refers to the practice of protecting individuals’ personal information from unauthorized access, use, disclosure, alteration, or destruction. It involves ensuring that individuals have control over their own personal data and that organizations that collect, store, and process personal data do so in a manner that respects individuals’ privacy rights.
Privacy laws differ across jurisdictions. In the U.S., the fragmented regulatory landscape includes comprehensive state-level consumer privacy acts, industry-specific federal laws, and intricate pre-emption relationships between.
The extent to which consumers have the right to make choices about their data depends heavily on the applicable laws.
If you include the location of the parties to the conversation in vCon’s metadata, it can help you identify which privacy and anti-wiretapping laws apply to the conversation, which is crucial for compliance.
What Data is Protected?
Not all data that businesses may have on individuals is protected. Data privacy laws protect personally identifiable information, meaning information that makes it possible to identify an individual or information about an “identified” or “identifiable” individual.
Data privacy laws do not apply to data that is publicly available, for example, because the person shared it on social media.
The scope of protected information varies depending on the applicable law and can include:
- Basic identifiers: Name, addresses (postal and email), government-issued identification numbers
- Digital identifiers: IP address (in some jurisdictions like California).
- Financial Data: financial account number or credit or debit card number, often in combination with any required security code or password that would permit access to a data subject’s financial account.
- Protected characteristics: Race, religion, disability, sexual orientation, national origin, etc.
- Consumer behavior: Purchase history, product interests, consumption patterns.
- Biometric data, including voiceprints, faceprints, fingerprints.
- Online activity: Browsing and search history, website and app interaction.
- Geolocation information
- Sensory information: Audio, visual, thermal, and olfactory data.
- Professional and educational information.
An important subset of PII constitutes “sensitive data” that is usually subject to a higher standard of protection. For example, it may require an opt-in consent for data collection and processing, and not just a notice. Sensitive information can include:
- Government-issued identifiers
- Health information
- Genetic data
- Financial data
- Biometric information, including faceprints and voiceprints used for identity recognition or verification
- Precise geolocation
- Log-in credentials
- Sexual behavior
- Citizenship and immigration status.
- Information about children and teens.
As of the time of writing, American Privacy Rights Act, an active bill, also seeks to define as sensitive certain private communications and online activity.
Communications Privacy
Communications privacy laws focus on the protection of private voice, video, and textual communications from unauthorized real-time interception and from unauthorized access when stored. Communications privacy laws are often called “anti-wiretapping” and “ant-eavesdropping” laws in different states.
Usually, communications are protected where there is a reasonable expectation of privacy. Customer service communications are not always protected. For example, one could reasonably infer from recent Illinois case law that on customer care calls, there may be no reasonable expectation of privacy because the customer care agent is expected to share the details of the conversation with the team to have the customer’s issue addressed (the case is Cook Au Vin, LLC v. Mid-Century Insurance Co., 2023 IL App (1st) 220601). Nonetheless, it is a good practice to disclose that the call may be recorded or if you may use a third-party vendor for call analytics.
Key Privacy Principles
Data privacy and communications privacy are guided by similar principles, emphasizing consent, transparency, and data minimization while balancing privacy rights with societal interests.
Key principles include:
- Notice/Transparency
Organizations must clearly disclose their data handling practices. This includes explaining what personal data is collected and for which purposes, how it is used, stored, and shared, and how consumers can exercise their data privacy rights. Privacy notices should be concise, transparent, and easily understandable. Changes to privacy practices should be promptly communicated, and in many cases, do not become effective unless the consumer has agreed to them. Notices must be provided at the time of data collection and on the website.
Communications privacy: Many states’ laws require that parties be notified if their communications are being recorded or monitored, often through audible beeps, verbal announcements, or visible signage. The unauthorized surveillance or interception of an individual’s private communications or activities is generally prohibited by law.
- Consent
Organizations need to obtain data subjects’ informed and freely given consent for collecting, using, storing, and sharing personal data. Different levels of consent may apply to different kinds of data or in different jurisdictions:
- Consent must be freely given, specific, informed, unambiguous, revocable, and documented.
When speaking of consent, it is worth mentioning that privacy regulations around the world often prohibit dark patterns – design practices that trick or manipulate users into making choices they would not otherwise have made and that may cause harm. Dark patterns include obscuring important information or preselecting options that frame information in a way that steers consumers toward making decisions more favorable for the business. Dark patterns are considered deceptive practices by the FTC and are illegal in the U.S.
- Consent can be affirmative (“opt-in” consent) or presumed unless stated otherwise (“opt-out” consent). Opt-in consent is usually required for sensitive data processing.
- Consent can be written, oral, or implied.
- Consent may not be required when processing is necessary to satisfy legal obligations or implement contracts or for law enforcement.
Communications privacy: Most laws stipulate that at least one party must consent to the recording or interception of a communication. Some jurisdictions require all parties to consent, known as “two-party” or “all-party” consent. The type of consent required (explicit or implied) may vary, but has to be obtained prior to the recording.
VCon allows storage of consent data, tracking permissions for specific data uses. Since for some purposes, consent can be given orally, vCons can store information about that consent within the call recording or call analytics, making consent management easier.

- Purpose, Collection, and Storage Limitation and Data Minimization:
Personal data should be collected for specific, explicit, and legitimate purposes and should not be used for purposes that are incompatible with those for which it was originally collected.
Organizations should collect only the minimum amount of personal data necessary to achieve the stated.
Personal data should be retained only for as long as necessary to fulfill the purposes for which it was collected, consistent with legal limitations and requirements. Organizations should establish retention policies and securely dispose of data that is no longer needed.
VCon permits masking and deletion of personally identifiable information, which reduces the amount of data processed and stored in accordance with this principle.
- Security
Appropriate technical, physical, and administrative measures must be implemented to protect covered data from unauthorized access and other risks. This may include encryption, access controls, and regular security assessments.
Most state data breach notification laws do not require breach notifications if the breached data was encrypted and the encryption key remained intact.
There are certain considerations around vCons and data security. Vcons can and in some cases should be encrypted (for example, if they contain unredacted sensitive information). Externally referenced files that are part of a vCon should be encrypted if they contain protected information and should be transported only over HTTPS. Finally, access to unredacted vCons and their referenced files should be restricted to authorized personnel only.

- Data Integrity
Personal data should be accurate, complete, up-to-date, and trustworthy throughout its lifecycle. The core principles of data integrity include consistency across systems, authenticity verification, and non-repudiation mechanisms.
VCons can be used to track conversational data provenance and ensure its integrity. VCons may be created and modified across different security domains and need to be protected against unauthorized modifications to ensure the authenticity of the conversational data. Before a vCon leaves its original security domain, it should be digitally signed to prevent alteration. Each domain should sign the vCon before transferring it to maintain the chain of trust.

- Accountability
Organizations are responsible for complying with data privacy laws and demonstrating compliance. This may involve conducting privacy impact assessments, appointing a data protection officer, and maintaining records of data processing activities.
7. Recordkeeping
Organizations are legally required maintain accurate logs of consumers’ profiles, data decisions, and data usage, including sales and marketing campaigns and instances of data disclosure to third parties.

Besides, some communications must also be preserved for compliance purposes in certain industries, such as banking and healthcare.
The ability to keep a record of the call’s contents, metadata, and attachments in a single “container” makes vCons useful for industries with strict record-keeping requirements (e.g., financial services and healthcare).

- Individual Rights
Across jurisdictions, individuals tend to have certain rights regarding their personal data:
- Access: Organizations should offer mechanisms for consumers to access and correct their personal data.
- Data Choices: Individuals often have the following data privacy rights:
- right to have their information deleted (also referred to as the “right to be forgotten”)
- right to port their data to a different data controller
- right to opt out of certain data practices, such as sale of their data, profiling, targeted/cross contextual behavioral advertising, automated decision-making.
- Breach Notification: Large amounts of data held by organizations attract cybercriminals, increasing the risk of data breaches. To mitigate the consequences of data breaches and incentivize advanced data security practices, most jurisdictions require prompt notification of affected individuals when breaches occur (within 30 days of discovery being the industry practice in the U.S.). This holds organizations accountable for data security and allows individuals to take protective actions.
- Non-Discrimination: Organizations must not discriminate against consumers who choose to exercise their data privacy rights.
Several of these rights, such as right of access, data choices (such as the right to be forgotten, the right to port the data to another vendor, and to opt out of certain data processing), and breach notification, require organizations to be able to quickly find what data is associated with a particular person.
Vcon contains information about parties to conversations and can contain call transcripts, making the search for a particular party easier.
What data is NOT protected?
A significant portion of business-related information falls outside the scope of data protection regulations. By carefully filtering out the legally protected elements from your dataset, you can retain a substantial amount of valuable information while simultaneously reducing your privacy compliance responsibilities.
The distinction between personal and nonpersonal information hinges on identifiability, meaning that personal data is identifiable and thus protected by most privacy laws when it can be reasonably linked to a particular person (or even a computer or a device).
When identifiable elements are removed from data, it becomes nonpersonal information, generally falling outside the scope of data privacy protection laws.
Some methods of transforming identifiable data into nonpersonal data are deidentification, anonymization, and aggregation.
Deidentification is the process of removing identifiable data from the dataset/document.
- It may take the form of information suppression (direct removal of identifying information),
- generalization (replacing a data element with a more general equivalent), or
- noise addition (slightly altering select data). Noise addition is used to ensure the privacy of individuals within a dataset while allowing for the extraction of useful statistical information by adding carefully calibrated noise to the data.
Sometimes it is possible to reidentify the deidentified data using other available information. In this context, although it is often used interchangeably with the term “deidentification,” the term “anonymization” refers to the more comprehensive irreversible removal of identifiable data. Rigorous deidentification or anonymization techniques should be employed to ensure that reidentification is either impossible or extremely difficult.
In the data privacy context, data aggregation is a data analytics process whereby combined data from multiple sources or individuals containing PII information is summarized, effectively removing PII from the final product. While aggregation can obscure individual identities, organizations must be vigilant not to allow re-identification.

Vcon offers a straightforward way to redact personally identifiable information from various media formats, including text, audio, video, and transcripts. vCon allows removing specific segments or entire recordings that could potentially be used for voice or facial identification. It is crucial for vCon implementers to ensure that their chosen redaction techniques effectively erase sensitive data while maintaining the overall integrity of the vCon.
Conclusion
While vCons are not a silver bullet for privacy compliance, they provide a robust framework that can significantly simplify and strengthen your privacy compliance efforts. The effectiveness of vCons is further enhanced by their compatibility with other protocols, such as SCITT (Supply Chain Integrity, Transparency, and Trust), which aids in establishing data provenance. By leveraging vCons, organizations can more effectively navigate the complex landscape of privacy regulations while maintaining the value of their customer data.
Diana James, CIPP/US would like to thank Thomas McCarthy-Howe for the opportunity to explore the privacy side of vCons in a co-authored draft Request for Comments that will soon be published on the Internet Engineering Task Force’s website. In the meantime, please feel free to get acquainted with the vCon documentation on IETF and GitHub.

